There is a new zeroday attack that is installing malware on a fully patched Window machine. It uses a vulnerability in all versions of Microsoft Word. The attack start with an e-mail, with a malicious Word document, once opened the exploit code downloads a malicious HTML application file that looks like a RTF document. Behind the scenes, the .hta file will download the malware.
This new attack stands out because it doesn’t require target to have macros enabled. Also it will open a decoy Word document to hide any sign of the attack.
Protecting against this tread
There is no patch yet available against this tread. Blocking all Word documents in Exchange is not a feasible option and warning you users to take extra caution before opening Word documents is not a real solution here.
So what can we do? We could simply block .hta files or mshta.exe from execution with applocker or SRP (Software Restriction Policies) to prevent execution of HTML apps.
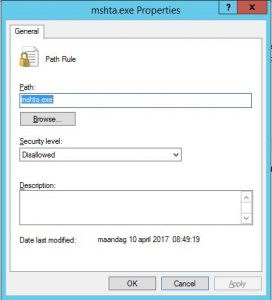
Create a GPO and go to :
- Computer configuration > Policies > Windows Settings > Security Settings > Software Restriction Policies > Additional Rules
- Create a New Path rule
- Path : mshta.exe
- Security level : Disallowed