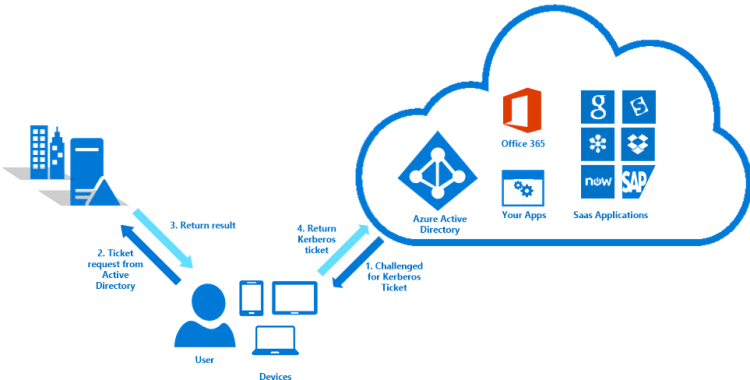
With the new version of Azure AD Connect you can enable the Single Sign-On option in combination with either Password synchronization or Pass-through Authentication. When enabled with Modern Authentication for Office 2016 users only have to type their username and do not need to type their password to sign in to Office applications of other cloud services when their machine is connected to the domain.
Setting up SSO with Password Sync
- Download the latest version of Azure Active Directory Connect. If you already have Azure AD Connect installed you can do an in-place upgrade and then reconfigure the settings.
- Logon as a domain administrator
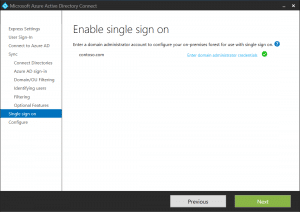
- Select Custom Installation so that you can enable Single Sign-On on the user sign-in page
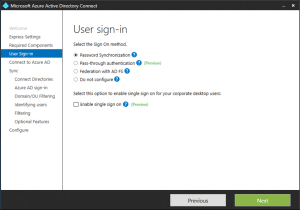
- Select Password Synchronization and Enable Single Sign on
- Click configure to finish the setup
Add endpoints to Intranet Zone
The following URL’s need to be explicitly added to the machine’s Intranet Zone. This settings makes sure that the browser sends the currently logged in user’s credentials in the form of Kerberos ticket to Azure AD.
Best way to do this is to create a GPO:
- Create a GPO that’s applied to all users or add it to an existing Internet Explorer settings GPO
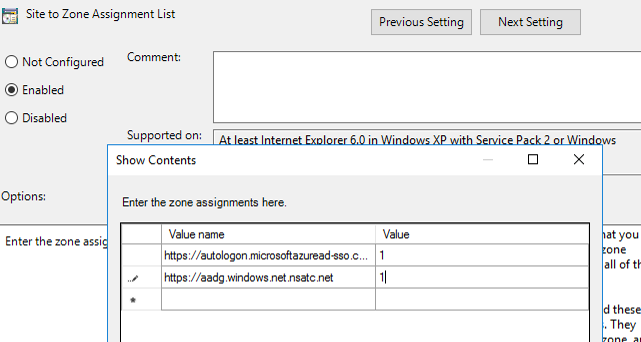
- Go to User Configuration\Administrative Templates\Windows Components\Internet Explorer\Internet Control Panel\Security Page and select Site to Zone Assignment List
- Enable to policy and add the following values:
- https://autologon.microsoftazuread-sso.com > 1
- https://aadg.windows.net.nsatc.net > 1
Modern Authentication
Modern Authentication in Office 365 is needed for users to experience the single sign-on feature in Outlook (Office 2013 / 2016) and Skype for Business. It also enables features like MFA (Multi Factor Authentication), Smart-Card and Certificate-based Authentication.
By default Modern Authentication is only enabled for Sharepoint-Online, for Exchange Online and Skype for Business it’s turned of.
Enable modern authentication for Exchange Online
Connect to Exchange Online Powershell, you can use this connector script or run the following code:
#Create credential object $credObject = Get-Credential #Import the Exchange Online ps session $ExchOnlineSession = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https://outlook.office365.com/powershell-liveid/ -Credential $credObject -Authentication Basic -AllowRedirection Import-PSSession $ExchOnlineSession
Run the following command the enable modern authentication
Set-OrganizationConfig -OAuth2ClientProfileEnabled $true
Verify the settings with
Get-OrganizationConfig | Format-Table -Auto Name,OAuth*
Enable modern authentication for Skype for Business
Connect to Skype for Business Online Powershell, or again use one the connector script.
#Create credential $credObject = Get-Credential #Import the Skype for Business Online PS session $sfbSession = New-CsOnlineSession -Credential $credObject Import-PSSession $sfbSession
Run the following command the enable modern authentication
Set-CsOAuthConfiguration -ClientAdalAuthOverride Allowed
And verify the settings with
Get-CsOAuthConfiguration
References and more informatie
If you want to know more about SSO and Modern Authentication you can check the following pages:
- https://docs.microsoft.com/en-us/azure/active-directory/connect/active-directory-aadconnect-sso
- https://support.office.com/en-us/article/Enable-Exchange-Online-for-modern-authentication-58018196-f918-49cd-8238-56f57f38d662?ui=en-US&rs=en-US&ad=US&fromAR=1
- https://social.technet.microsoft.com/wiki/contents/articles/34339.skype-for-business-online-enable-your-tenant-for-modern-authentication.aspx




Hallo Ruud,
The domain & tenant I tried your commands on has AAD Connect & password hash sync & single sign-on enabled through the AAD connect wizard. Also 2FA is enabled.
Also: I’m a PS newbie.
While trying to connect to the O365 services with PS I get errors like:
Connect-AzureAD : One or more errors occurred.: AADSTS50076: Due to a configuration change made by your administrator, or because you moved to a new location, you must u
se multi-factor authentication to access ‘00000002-0000-0000-c000-000000000000’.
Trace ID: 6ab93417-1b1c-436f-8a6c-c3f267311e00
Correlation ID: 5fb369b8-fd18-4032-ab62-57158eb9d6f7
Timestamp: 2019-08-07 13:11:06Z
At line:1 char:1
+ Connect-AzureAD -Credential $credential
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : AuthenticationError: (:) [Connect-AzureAD], AadAuthenticationFailedException
+ FullyQualifiedErrorId : Connect-AzureAD,Microsoft.Open.Azure.AD.CommonLibrary.ConnectAzureAD
Connect-AzureAD : One or more errors occurred.
At line:1 char:1
+ Connect-AzureAD -Credential $credential
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : AuthenticationError: (:) [Connect-AzureAD], AggregateException
+ FullyQualifiedErrorId : Connect-AzureAD,Microsoft.Open.Azure.AD.CommonLibrary.ConnectAzureAD
It seems I need to use other methods to connect to a tenant once it has AAD Connect, SSO and 2FA enabled. Any suggestions?
Thanks for any useful guidance.
Regards,
Bavo
Can’t you use the Microsoft app password? I use it a lot with PowerShell scripts if MFA isn’t working / showing the dialog