When you are away from home you might need to have access to your home network, to get files from your NAS for example. Or when you are on a public WiFi, you probably want to use a secure VPN connection before you access your bank account. With UniFi VPN we can arrange all this.
With UniFi network we can easily set up a remote access VPN server on our UDM Pro or USG. The remote VPN doesn’t only offer you access to your home network but also allows you to safely browse the internet.
Tip
Make sure that you also check out this UniFi Teleport article, which allows you to create a VPN connection from your mobile device with one click.
In this article, I am going to explain how to set up UniFi VPN on the latest UniFi Network version (7.x) and we will take a look at some common issues.
Configure UniFi VPN
To configure the UniFi VPN you will need to have a UDM model or a USG. Also, make sure that you run the latest firmware on your console.
If you have a modem or router before your UDM or USG, then make sure that the modem/router is set into Bridge mode. This way all traffic will be forwarded directly to your Unifi Network. If that isn’t possible, then you will need to forward the following port numbers to your Unifi Network console:
– UDP port 500
– UDP port 4500
- Open the VPN Settings
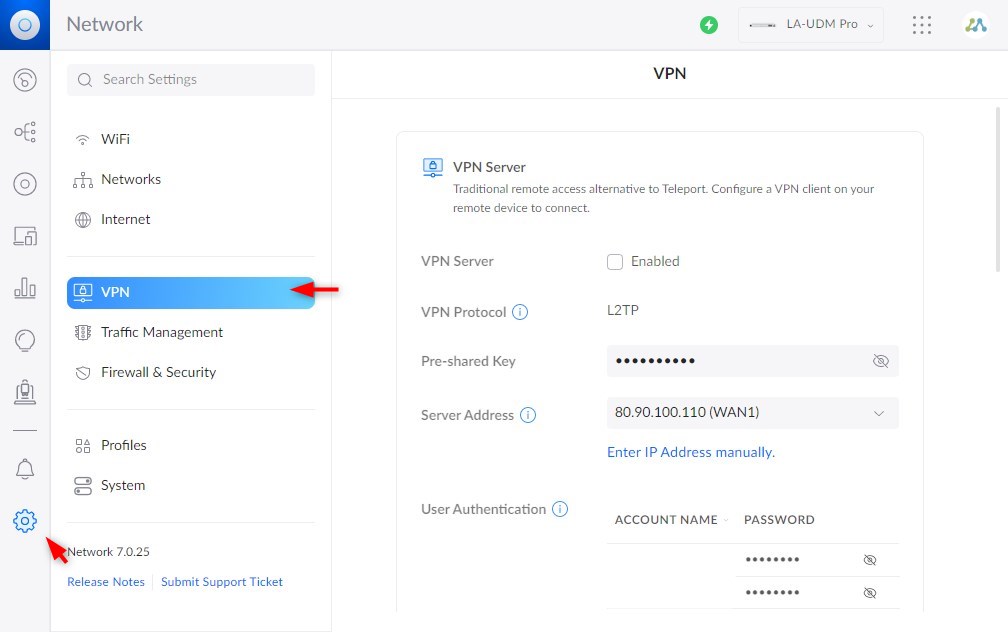
In the UniFi network app, go to Settings > VPN
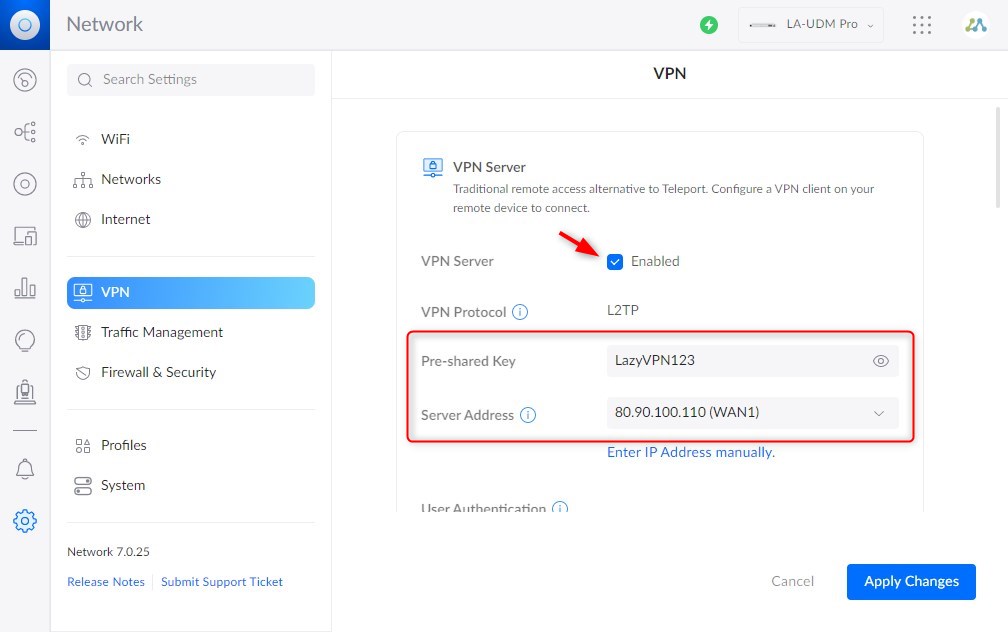
- Enable VPN Server
Enable the VPN Server and note or change the Pre-shared Key
Make sure that the Server Address is set to your Public IP Address - Create a new VPN user
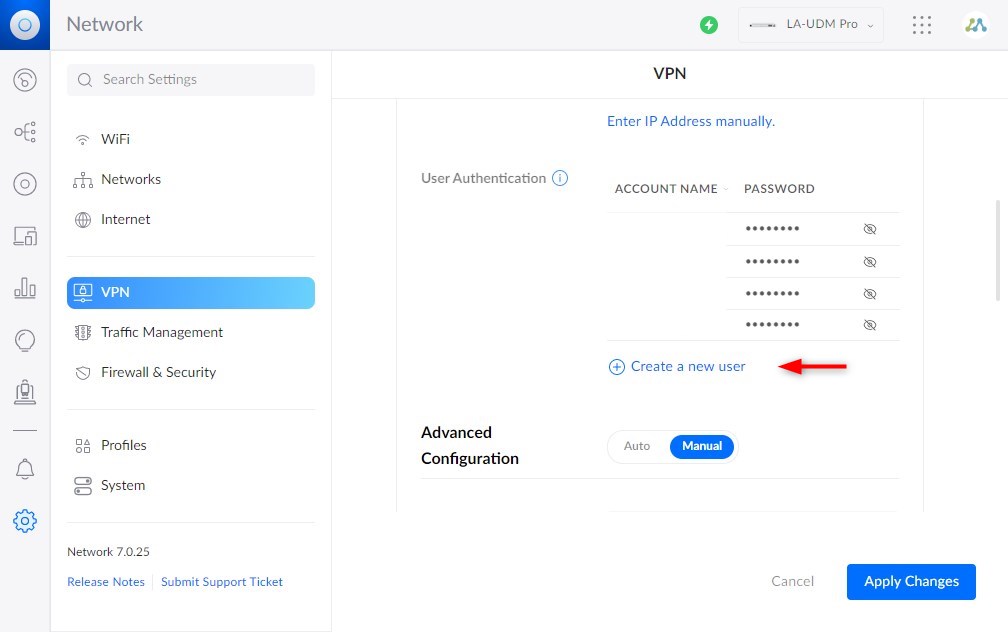
The next step is to create a new VPN user. Click on Create a new user and enter a username and password.
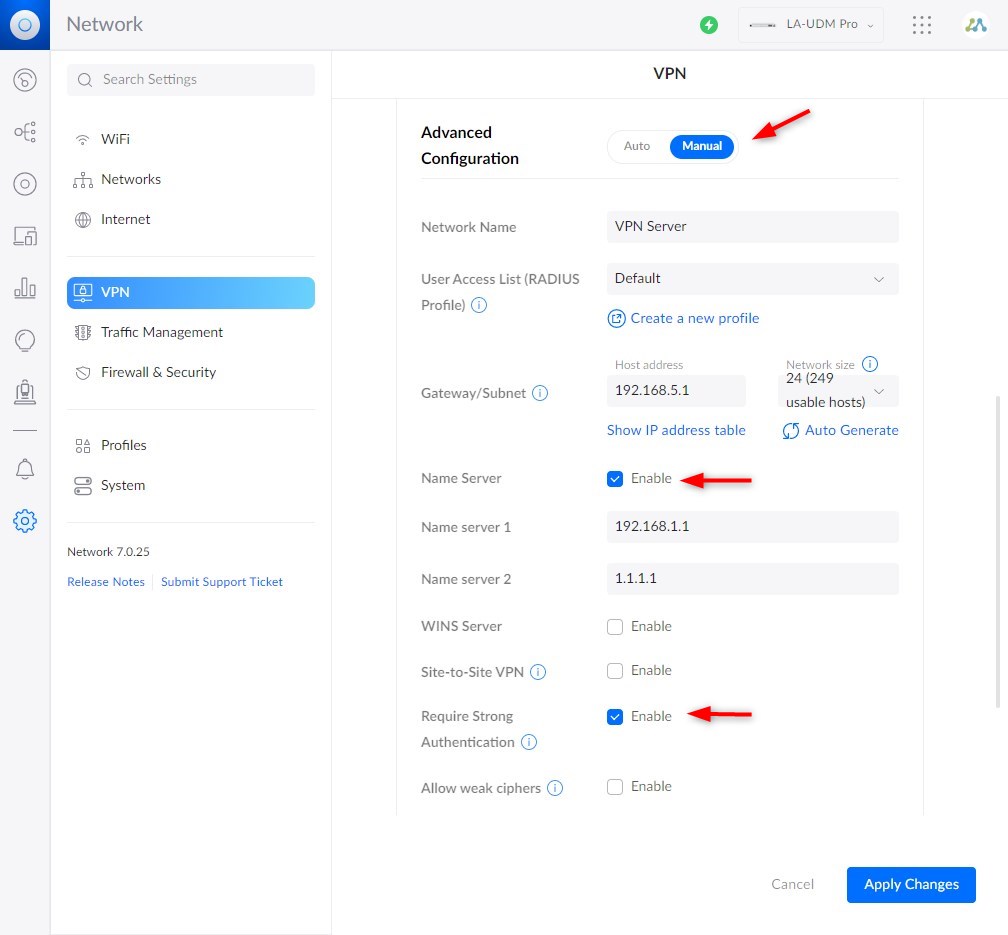
- Advanced Configuration
Set the advanced configuration to Manual. Here you can change the subnet if you need. But more important is to set your internal DNS server and enable Require Strong Authentication.
Strong Authentication is needed for the MS-Chap v2 protocol that is used by Windows 10 and 11.
Firewall rules are automatically created for the Remote access VPN, so we don’t need to look at them.
Connecting to UniFi VPN with Windows
To use the VPN connection on Windows you don’t need to install any clients. We can use the built-in VPN client. The steps below are the same on Windows 10 and 11.
- Open Start and type VPN and select VPN Settings
- Click Add VPN
- Select Windows (built-in) as VPN provider
- Enter a connection name, it can be anything you like
- Enter the public IP Address of your UniFi Console

- VPN Type > Select L2TP/IPSec with pre-shared key
- Enter the pre-shared key that we have set earlier in the UniFi Console
- Fill in the username and password that we created.
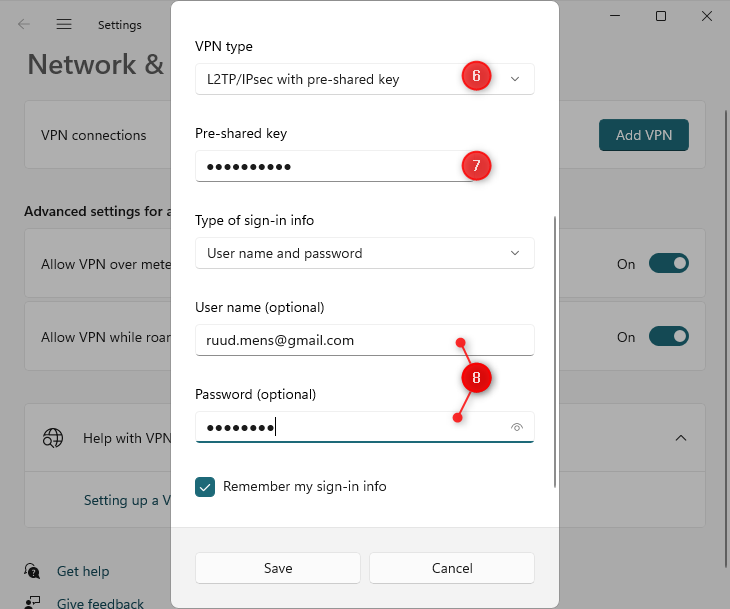
- Save the settings
- Next, we need to change the VPN Network adapter, to enable MS Chap v2.
Press Windows key + R and type ncpa.cpl <enter> - You will now see your VPN network adapter.
Right-click on your adapter and select Properties - On the Security tab:
select Allow these protocols and enable Microsoft CHAP Version 2

- Click Ok to save the settings.
- You can now click on Connect to test the VPN Connection. It should immediately connect to your UniFi VPN server.
As you can see in the screenshot below we have connected the Lazy VPN connection and got an IP Address in the range as configured in the UDM:

Troubleshoot UniFi VPN connection issues
Setting up remote access VPN can sometimes be a bit challenging. When your UDM or USG is located behind a modem/router then L2TP VPN connections sometimes won’t work as easily as they should.
Besides potential modem/router issues also the client can cause issues with setting up a remote VPN connection. For example, at the beginning of 2022, a Windows 10 and 11 update (KB5009543, KB5009566) cause the following connection error:
The L2TP connection attempt failed because the security layer encountered a processing error during initial negotiations with the remote computer
It was fixed with a new update, but as you can see it can also be the client that is the issue.
So to help you debug connection issues you can monitor the VPN log on your UDM/USG. This will really help you with finding the cause of the connection issue:
How to Open VPN Log on UDM/USG
To view the VPN log you will need to have SSH access to your UDM or USG. Make sure the SSH access is enabled in the UniFi OS and that you know the password:

Open the Windows Terminal or any other CLI that you like to use and type:
# Replace the IP Address with the address of your USG/UDM ssh root@192.168.0.1 # Enter the SSH Password
Next, we will open the L2TP VPN Log in the console. This will live stream the content from the log into the console:
sudo swanctl --log

It’s normal that you don’t see any results in the beginning. Just leave the console open and try to connect your VPN Client.
No VPN Log Output
When you try to connect the client but don’t see any output in the console, then the VPN Client is unable to reach the console. Make sure that you use the correct public IP Address, port forwarding is set correctly, and rechecked the VPN configuration in the UniFi Console.
Wrong Preshared key
If the preshared key is wrong for example, you will see the following in the log:
02[ENC] generating ID_PROT response 0 [ KE No NAT-D NAT-D ] 02[NET] sending packet: from 80.90.100.110[500] to 192.168.1.22[60815] (372 bytes) 04[NET] received packet: from 192.168.1.22[60816] to 80.90.100.110[4500] (76 bytes) 04[ENC] invalid ID_V1 payload length, decryption failed? 04[ENC] could not decrypt payloads 04[IKE] message parsing failed
Wrong Username or Password
When the username or password is wrong, you will get a remote connection was denied error on the client. In the VPN log we can identify it by the following lines:
16[IKE] received DELETE for ESP CHILD_SA with SPI c707898e
16[IKE] closing CHILD_SA lns-l2tp-server{7} with SPIs c577f0d2_i (771 bytes) c707898e_o (494 bytes) and TS 87.214.43.90/32[udp/1701] === 192.168.1.22/32[udp/1701]
16[CHD] updown: ok
09[NET] received packet: from 192.168.1.22[54205] to 87.214.43.90[4500] (92 bytes)
09[ENC] parsed INFORMATIONAL_V1 request 2150840229 [ HASH D ]
09[IKE] received DELETE for IKE_SA lns-l2tp-server[7]
Wrapping UP
Setting up remote access VPN can sometimes be a bit challenging. Especially when your USG or UDM is behind another modem or router. But once connected you can securely access your home network or browse the internet safely by routing your internet traffic over the VPN.
I hope you found this article useful, if you have any questions just drop a comment below.





Is it possible for a streaming device to connect to the UDM Pro VPN? Where would I enter the key, username, and password on the AppleTV (for example)? Thank you!
Nice article and step by step instructions. Worked for me. I was able to setup a vpn and map a network drive on another vlan. The network drive is accessible from the in-house computers. Now my remote laptop is able to access the same network drive through a vpn. Traffic Rules were setup in UDM to allow access from VPN-Vlan to the vlan that has the drive.
Along the way, I discovered that ubiquit guest wifi does not allow a vpn pass through. Neither does the hotspot from my mobile.
Many people tell me that USG and UDM *cannot* put my Remote Users in the same CIDR block as my LAN! If this is the case, how am I supposed to mount and NFS/SMB share, or use ScreenSharing from my remote Mac on my LAN Macs?! This was a relative no-brainer with EdgeRouter, although it did require hacking in the CLI.
Everybody claims that it will give you access to your land, but I don’t see how that’s possible if you’re stuck into a separate private IP block. Actual *access to my LAN* requires me to be on the same CIDR block.
I tried manually setting that IP addresses in the VPS subnet section, but when I put in my LAN’s CIDR It’s screams at me that this is not allowed! My head is a soft as a rotten tomato fruit beating it against the wall over this.
Hi Rudy,
Thanks for explaining how to set up a VPN.
Got it working really quickly from my iPhone, it proves the VPNsetup is correct.
But when I connect my laptop (win11) to my iPhone hotspot and try to setup a vpn connection from my laptop it wont work.
It also doenst work from a public WiFi network.
I dont get it, why can I make a vpn connection from my iphone without any portforwards but when I connect my laptop through the hotspot on my iPhone (5G network) it wont connect.
Opening the UDP port 500 and UDP port 4500 cannot be done in the unifi controller it creates a conflicts with IPsec (ports 500 and 4500).
Can you tell me what to do?
The scenario what I want to accomplish is:
– iPhone Hotspot (5G network)
– Connect laptop (win11) to the iphone Hotspot.
– Start VPN connection from the laptop.
Or
– Connect laptop (win11) to public WiFi network.
– Start VPN connection from the laptop.
Thanks in advance
I have a DM Pro configured for VPN. I’m running Windows 10 Pro on a desktop. I can connect to the DM Pro from home with admin credentials but not with anything else. The other admin at work tried to connect using the same inputs I used and his came back with “The connection was prevented because of a policy configured on your RAS/VPN server. Specifically, the authentication method used by the server to verify your username and password may not match the authentication method configured in your connection profile. Please contact the Administrator of the RAS server and notify them of this error. (Error 812)”. I tried to set up a new profile on my computer using different credentials and got the same error message. We are trying to connect using different locations (ip’s) he from his home and me from mine. Do you possibly have a solution?
Last weekend transferred to another ISP. Since then my VPN won’t work on 1 of the laptops. 1 laptop is running on Windows 10, works fine. The other is running on Windows 11 and I get the following notification: “The L2TP connection attempt failed because the security layer encountered a processing error during initial negotiations with the remote computer”
My first thought was that is maybe was something caused by an Windows 11 update, but when I’m on the WiFi hotspot on my phone, it works fine. The new ISP gave me an modem where IPv6 is enabled, most solutions on the internet adviced to turn it of on the laptop. Worked for the Windows 10 laptop, but not for the Windows 11 laptop.
Got an LOG from the UDM Pro, do I miss something?
11[NET] received packet: from 210.62.215.173[500] to 192.168.18.26[500] (408 bytes)
11[ENC] parsed ID_PROT request 0 [ SA V V V V V V V V ]
11[ENC] received unknown vendor ID: 01:52:8b:bb:c0:06:96:12:18:49:ab:9a:1c:5b:2a:51:00:00:00:01
11[IKE] received MS NT5 ISAKMPOAKLEY vendor ID
11[IKE] received NAT-T (RFC 3947) vendor ID
11[IKE] received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
11[IKE] received FRAGMENTATION vendor ID
11[ENC] received unknown vendor ID: fb:1d:e3:cd:f3:41:b7:ea:16:b7:e5:be:08:55:f1:20
11[ENC] received unknown vendor ID: 26:24:4d:38:ed:db:61:b3:17:2a:36:e3:d0:cf:b8:19
11[ENC] received unknown vendor ID: e3:a5:96:6a:76:37:9f:e7:07:22:82:31:e5:ce:86:52
11[IKE] 210.62.215.173 is initiating a Main Mode IKE_SA
11[CFG] selected proposal: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048
11[ENC] generating ID_PROT response 0 [ SA V V V V ]
11[NET] sending packet: from 192.168.18.26[500] to 210.62.215.173[500] (160 bytes)
10[NET] received packet: from 210.62.215.173[500] to 192.168.18.26[500] (388 bytes)
10[ENC] parsed ID_PROT request 0 [ KE No NAT-D NAT-D ]
10[IKE] remote host is behind NAT
10[ENC] generating ID_PROT response 0 [ KE No NAT-D NAT-D ]
10[NET] sending packet: from 192.168.18.26[500] to 210.62.215.173[500] (372 bytes)
13[NET] received packet: from 210.62.215.173[4500] to 192.168.18.26[4500] (76 bytes)
13[ENC] parsed ID_PROT request 0 [ ID HASH ]
13[CFG] looking for pre-shared key peer configs matching 192.168.18.26…210.62.215.173[192.168.178.119]
13[CFG] selected peer config “lns-l2tp-server”
13[IKE] schedule delete of duplicate IKE_SA for peer ‘192.168.178.119’ due to uniqueness policy and suspected reauthentication
13[IKE] IKE_SA lns-l2tp-server[21627] established between 192.168.18.26[192.168.18.26]…210.62.215.173[192.168.178.119]
13[IKE] scheduling reauthentication in 2613s
I think that it not good advise to tell people to put their router in bridge mode, this effectively means there is no NATing between the router and the internet, leaving their network open to any incoming connection.
Script kiddies can probe away all day long looking for an open port
Punching holes through the router is the preferred option, which is what you said to do but only if bridge mode doesn’t work
Do you know of a VPN client that can be used for Samsung mobiles?
Samsung in their stupidity has not bothered to support L2TP on it’s VPN client, crazy I know, but that’s my understanding
The UDP Pro has a built-in firewall, so using bridge mode should not be a problem. Sure, two firewalls might be safer, but if you open up ports, and don’t configure the client behind it correctly then you still have a problem.
I don’t know a good VPN client for Samsung mobile, sorry.
So wondering if you’ve experienced the issue where 2 remote users cannot connect to l2tp vpn from the same remote location/ip? We’ve been using l2tp on a usg for a while and it works well except for this issue.
see thread https://community.ui.com/questions/When-is-strongSwan-being-updated-on-USG-firmware/6c337ff6-8bd5-4e67-903b-5da42f99f8fd?page=1
I want the UDM pro to connect to a VPN and rout all traffic over that. I have a UDM pro at the main office and branch office. I want one lan.
Anyone have an idea what could be going wrong here? Using the standard VPN client on my iPhone and a USG at home. When I am connected to WiFi network (the same network where the USG and VPN is running: I cannot connect and get a timeout.
05[IKE] 192.168.1.215 is initiating a Main Mode IKE_SA
05[ENC] generating ID_PROT response 0 [ SA V V V ]
05[NET] sending packet: from 10.20.30.40[500] to 192.168.1.215[500] (136 bytes)
14[NET] received packet: from 192.168.1.215[500] to 10.20.30.40[500] (356 bytes)
14[ENC] parsed ID_PROT request 0 [ KE No NAT-D NAT-D ]
14[ENC] generating ID_PROT response 0 [ KE No NAT-D NAT-D ]
14[NET] sending packet: from 10.20.30.40[500] to 192.168.1.215[500] (372 bytes)
03[NET] received packet: from 192.168.1.215[500] to 10.20.30.40[500] (108 bytes)
03[ENC] invalid ID_V1 payload length, decryption failed?
03[ENC] could not decrypt payloads
03[IKE] message parsing failed
03[ENC] generating INFORMATIONAL_V1 request 348789406 [ HASH N(PLD_MAL) ]
03[NET] sending packet: from 10.20.30.40[500] to 192.168.1.215[500] (76 bytes)
03[IKE] ID_PROT request with message ID 0 processing failed
08[NET] received packet: from 192.168.1.215[500] to 10.20.30.40[500] (108 bytes)
08[ENC] invalid ID_V1 payload length, decryption failed?
08[ENC] could not decrypt payloads
08[IKE] message parsing failed
08[ENC] generating INFORMATIONAL_V1 request 2321790578 [ HASH N(PLD_MAL) ]
08[NET] sending packet: from 10.20.30.40[500] to 192.168.1.215[500] (76 bytes)
08[IKE] ID_PROT request with message ID 0 processing failed
16[NET] received packet: from 192.168.1.215[500] to 10.20.30.40[500] (108 bytes)
16[ENC] invalid ID_V1 payload length, decryption failed?
16[ENC] could not decrypt payloads
16[IKE] message parsing failed
16[ENC] generating INFORMATIONAL_V1 request 2107681205 [ HASH N(PLD_MAL) ]
16[NET] sending packet: from 10.20.30.40[500] to 192.168.1.215[500] (76 bytes)
16[IKE] ID_PROT request with message ID 0 processing failed
14[NET] received packet: from 192.168.1.215[500] to 10.20.30.40[500] (108 bytes)
14[ENC] invalid ID_V1 payload length, decryption failed?
14[ENC] could not decrypt payloads
14[IKE] message parsing failed
14[ENC] generating INFORMATIONAL_V1 request 3739752759 [ HASH N(PLD_MAL) ]
14[NET] sending packet: from 10.20.30.40[500] to 192.168.1.215[500] (76 bytes)
14[IKE] ID_PROT request with message ID 0 processing failed
08[NET] received packet: from 192.168.1.215[500] to 10.20.30.40[500] (108 bytes)
08[ENC] invalid ID_V1 payload length, decryption failed?
08[ENC] could not decrypt payloads
08[IKE] message parsing failed
08[ENC] generating INFORMATIONAL_V1 request 2608692470 [ HASH N(PLD_MAL) ]
08[NET] sending packet: from 10.20.30.40[500] to 192.168.1.215[500] (76 bytes)
08[IKE] ID_PROT request with message ID 0 processing failed
16[JOB] deleting half open IKE_SA after timeout
But when I turn off WiFi on my iPhone and am connected to the cellular network of my provider the VPN works like a charm:
02[IKE] 50.60.70.80 is initiating a Main Mode IKE_SA
02[ENC] generating ID_PROT response 0 [ SA V V V ]
02[NET] sending packet: from 10.20.30.40[500] to 50.60.70.80[18834] (136 bytes)
08[NET] received packet: from 50.60.70.80[18834] to 10.20.30.40[500] (356 bytes)
08[ENC] parsed ID_PROT request 0 [ KE No NAT-D NAT-D ]
08[IKE] remote host is behind NAT
08[ENC] generating ID_PROT response 0 [ KE No NAT-D NAT-D ]
08[NET] sending packet: from 10.20.30.40[500] to 50.60.70.80[18834] (372 bytes)
15[NET] received packet: from 50.60.70.80[18835] to 10.20.30.40[4500] (108 bytes)
15[ENC] parsed ID_PROT request 0 [ ID HASH N(INITIAL_CONTACT) ]
15[CFG] looking for pre-shared key peer configs matching 10.20.30.40…50.60.70.80[10.63.235.195]
15[CFG] selected peer config “remote-access”
15[IKE] IKE_SA remote-access[3] established between 10.20.30.40[10.20.30.40]…50.60.70.80[10.63.235.195]
15[ENC] generating ID_PROT response 0 [ ID HASH ]
15[NET] sending packet: from 10.20.30.40[4500] to 50.60.70.80[18835] (76 bytes)
01[NET] received packet: from 50.60.70.80[18835] to 10.20.30.40[4500] (396 bytes)
01[ENC] parsed QUICK_MODE request 2210812780 [ HASH SA No ID ID NAT-OA NAT-OA ]
01[IKE] received 3600s lifetime, configured 0s
01[ENC] generating QUICK_MODE response 2210812780 [ HASH SA No ID ID NAT-OA NAT-OA ]
01[NET] sending packet: from 10.20.30.40[4500] to 50.60.70.80[18835] (204 bytes)
14[NET] received packet: from 50.60.70.80[18835] to 10.20.30.40[4500] (60 bytes)
14[ENC] parsed QUICK_MODE request 2210812780 [ HASH ]
14[IKE] CHILD_SA remote-access{1} established with SPIs c8c931a9_i 0ff690dc_o and TS 10.20.30.40/32[udp/l2f] === 50.60.70.80/32[udp/57885]
06[KNL] 10.255.255.0 appeared on ppp1
15[KNL] 10.255.255.0 disappeared from ppp1
02[KNL] 10.255.255.0 appeared on ppp1
16[KNL] interface l2tp0 activated
Tested it with Samung TAB A8 tablet as well, same issue. When on WiFi the VPN is not connecting, when connected to other WiFi or cellular network the VPN works.
Anyone any idea?
Hi Marcel
This behaviour is by design, you cannot connect to the VPN as you are already part of the network the VPN will join you to.
Stewart
How do I run my network traffic through a separate vlan that connects to an outside vpn service link nordvpn or vpnunlimited on udmp?
Following up on my question about using Intune/Endpoint Manager to distribute the setup: not possible, but it is relatively easy to do using PowerShell, e.g.:
Install-Module -Name VPNCredentialsHelper -Confirm:$False -Force
Set-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Services\PolicyAgent” -Name “AssumeUDPEncapsulationContextOnSendRule” -Value 2
Add-VpnConnection -Name “VPN Name” -ServerAddress “AAA.BBB.CCC.DDD” -EncryptionLevel “Required” -L2tpPsk “pskkey” -Force -RememberCredential -IdleDisconnectSeconds 0 -TunnelType “L2tp” -AuthenticationMethod “MSChapv2”
Set-VpnConnectionUsernamePassword -connectionname “VPN Name” -username “XXXX” -password “XXXXX”
Where:
VPN Name = Name of the connection as it should appear in Windows
AAA.BBB.CCC.DDD = Public IP address of the UDM
pskkey = VPN’s shared key as defined in UDM
XXXX = VPN username as defined in UDM (case sensitive!)
XXXXX = VPN password as defined in UDM (case sensitive!)
The Set-ItemProperty registry setting step may or may not be required, depending on your local internet connection setup: https://docs.microsoft.com/en-US/troubleshoot/windows-server/networking/configure-l2tp-ipsec-server-behind-nat-t-device
Thank you for the write up. I’ve been looking for a good one! Keep it up!
No problem, happy to give something back!
Very useful article – it works! I have quite a few users to roll out the VPN connection to…is there a way to do this in Intune/Microsoft Endpoint Manager? Intune requires the use of the EAP XML method
Haven’t looked into that
hi there. how can I setup VPN so the remote computer can have the same ip address subnet as a computer on my local network? for example 192.168.1.10 (remote host ) and 192.168.1.20 (lan computer) the reado is that I got a client-server software that only allows connections for computers on the same ip range/subnet. can I have the lan computer on the VPN subnet?
In step 4, use the same subnet as your local LAN. But make sure that you split the range. So use 192.168.1.10 – 199 for your local LAN DHCP and 192.168.1.200 – 192.168.1.220 for your VPN clients for example.
After completing this setup, I’m able to connect no problem and I’m routing out the remote gateway per default setup however I am unable to access any LAN devices. I’ve used these instructions on a couple of different UDM Pro devices with the same results.
I just got this working, connecting to my network from a laptop tethered to a phone.
In step 2, enable VPN, the server address now shows “Auto Defined (WAN1)” in my case, it wouldnt work. The trick is to “Enter IP Address Manually”. Clicking this populated the public IP address. Save.
Connects great now.
Thank you Rudy. Nice article by the way.
I desire to use my PC to connect to my UDM-Pro configured with DDNS through the internet. I definitely desire to access the UDM-Pro management GUI, but also be able to access devices (such as sysnology NAS, security camera controller,…) configured on different VLANs.
I am hoping to gain access to my entire network with this 1 VLAN connection. How would I allow access through the management function.. or what settings are you referring to? Thanks,
If your network has VLANs, does the Unifi VPN server allow access to all of them? If yes, are there any configurations needed to do this?
Yes, that is possible. Depending on your current configuration you will need to allow access through the traffic management function.