In the last couple of weeks, I have been working on deploying Office 365 Multi-Factor Authentication. The main challenge was not the setup of MFA in Office 365, but with deploying this in our organization was to inform our users, so we don’t get too many helpdesk tickets once MFA is enabled, and to come up with a good rollout plan.

In this article, I will walk you through the setup process of Office 365 multi-factor authentication and give you some tips on how to roll it out in your organization.
Note
Make sure that you have enabled modern authentication. Especially in older tenants this needs to be enabled manually.
Office 365 MFA License
Before we start with the setup of MFA in Office 365, we will take a quick look at the license. Multi-factor authentication is part of the Microsoft 365 business (and Office 365) plans. With Office 365 MFA you can only protect Office 365 applications.
This means that all Office 365 Online applications are protected and also the OneDrive client and Outlook application. What isn’t protected with MFA is, for example, logging in on your computer.
Multi-Factor Authentication for Office 365 doesn’t offer all the security features that are available in the Azure MFA version. But more than enough for a good additional security layer on your user sign-ins.
The following features are available:
- Mobile app (Microsoft Authenticator app)
- Phone call
- SMS
- App password for clients that don’t support MFA (Gmail app on Android for example)
- Remember MFA for trusted devices
One of the features that I really miss compared to the Azure MFA version is the One-Time bypass and the Trusted IPs.
Setup mfa office 365
You need to be tenant Admin to set up MFA for your Office 365 tenant.
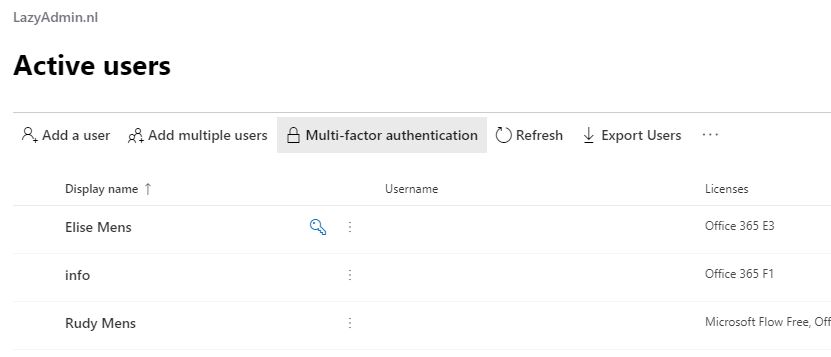
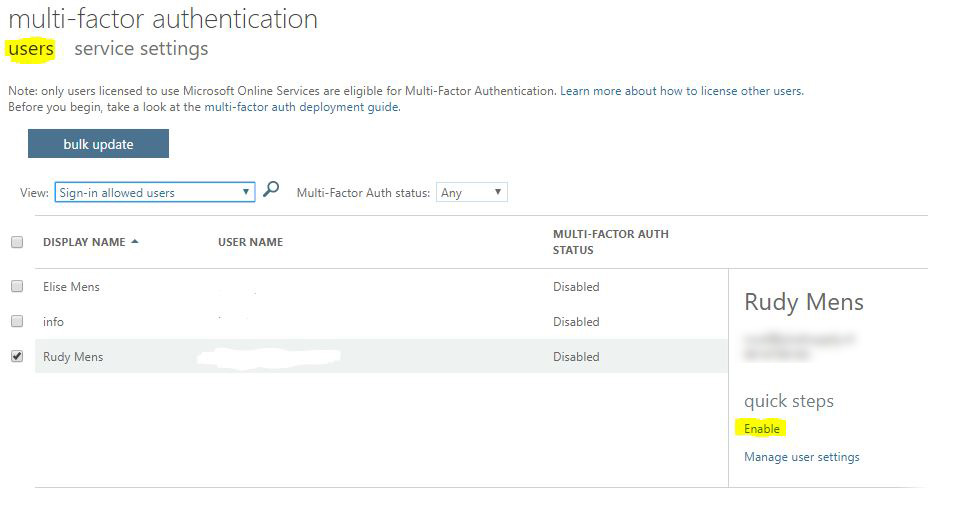
- Open the Admin Center and go to Users > Active Users
- Open Multi-factor authentication
Don’t select any user yet, just open the Multi-factor authentication screen. You will find the button in the toolbar.
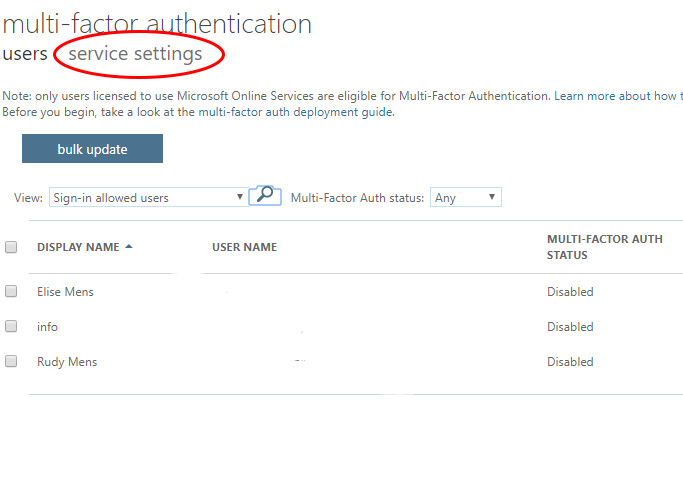
- Open the Service settings
Before we start enabling MFA for the users, we first go through the service settings. The button to the settings screen doesn’t stand out, but it’s just below the title
- Setup MFA Office 365
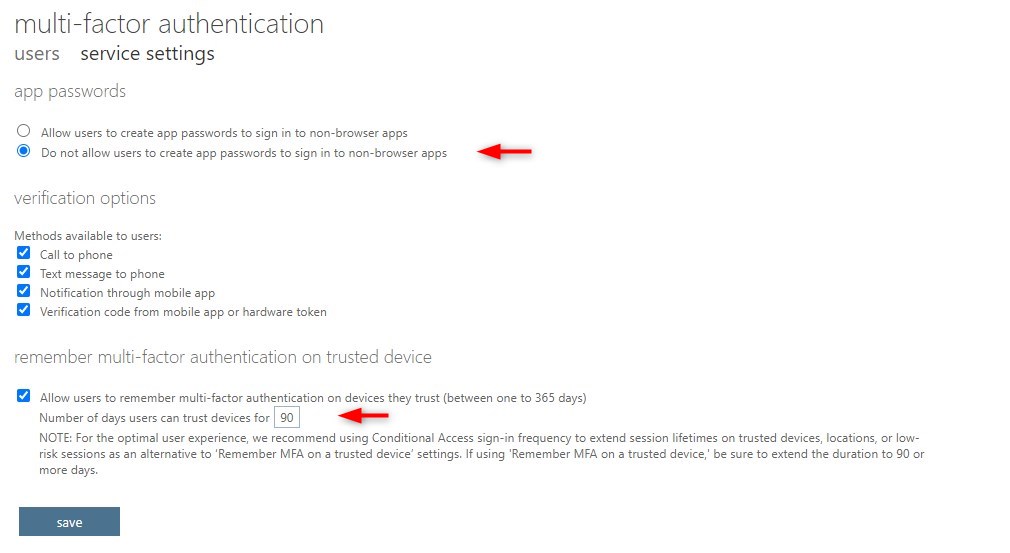
A few settings are important here:
Make sure you check “Do not allow user to create App password”. This is only needed for apps that don’t support multi-factor authentication. You should prevent the use of these kinds of apps in your tenant.
Cell to phone and text message to phone is also less secure. Only enable them when you really need them.
Make sure that trusted devices is set to 90 days atleast. - Enable MFA for Office 365 users
After you have set the settings to your liking click on save and then on users (just below the title Multi-factor authentication).
You see the list of your users again. Here you can select single or multiple users to enable MFA.
At the moment you enable Office 365 MFA for a user it can get the setup screen as soon as the users browse to one of the Office 365 products.
Using the bulk update feature
You can also enable multi-factor authentication with the bulk update feature. This works with a simple excel file containing the usernames and the required status (enable, disable). Just click on the bulk update button and download the sample file
Using PowerShell to enable MFA
Another option is to use PowerShell to enable MFA. The advantage of using PowerShell is that you can automate it, so you never forget the enable it for a user.
I have created a small script to enable MFA with PowerShell that you can find here. I also created a script to get the MFA status of your users that you can find in this article.
Enable Location and Number Matching
By default, the MFA request on your phone only asks if you want to improve or deny the request. You can’t see where the request is coming from, which is a security risk.
To mitigate the risk, you can enable number matching and/or add additional context (location and app) to the MFA request.
Read more about those features in this article.
Planning the roll-out
When you enable MFA for a user it will, at the next login, get a screen that additional security measure is required. So make sure you have informed your user upfront with a clear user guide on the steps they have to take.
Some of the fall pits I come across are:
- Some users didn’t notice they had to select the mobile app in step 1. So they got an SMS text which isn’t really user-friendly
- Make sure your users select “Receive notification for verification“
- Users with an Apple need to allow push notification for the Microsoft Authenticator app. Not all Apple users know where to find that (resulting in helpdesk calls)
- If users start the MFA process them self, through https://aka.ms/mfasetup, they can’t create an app password immediately
Create I pilot group with different types of users. I start with 15 users spread across the company to test MFA for 6 weeks. This allowed me to improve the manual and detect any issues that might come up.
If you have a large organization make sure you roll it out in batches. No matter how good the manual is, it will result in a raise in helpdesk tickets.
Changing user preferences
Users can easily change their preferences or manage the connected mobile phone(s) through their Office 365 account page. Also, the creating of an additional app password can be done here by the user self.
- Login at myaccount.microsoft.com
- Go to Security Info in the menu on the left side
At the top, you can change the Default sign-in method. The most user-friendly option here is to use the Microsoft Authenticator – Notification.
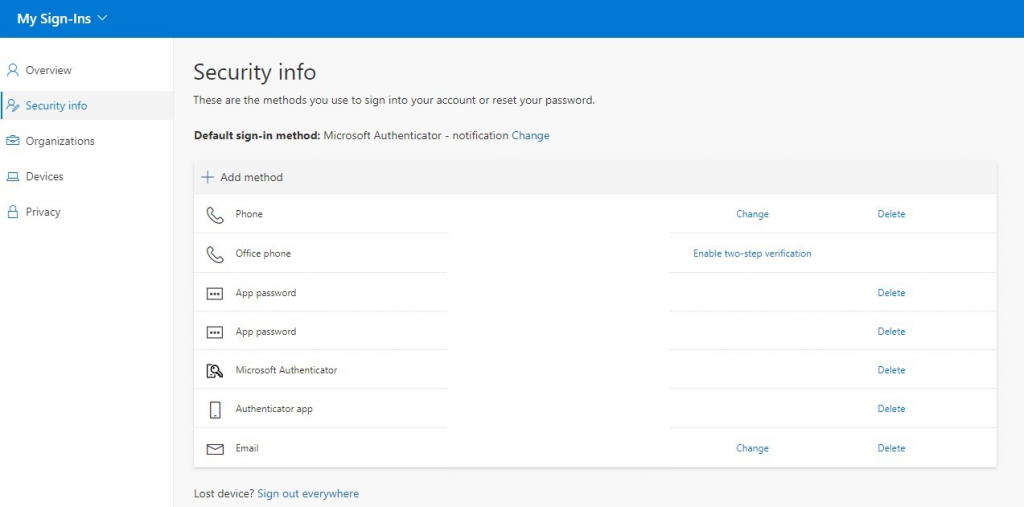
In the list you can add different authentication methods, which is always a good idea to have in case the app isn’t working or if you have switched phone and the app is not been installed yet.
The user can create an app password. One password can be used for multiple applications, but it is better to create unique app passwords for every application that can’t handle MFA.
Conclusion
There is no reason not to use multi-factor authentication in Office 365. The setup is done in a couple of minutes and the user impact is minimal. It adds an additional layer of security to a part of your IT environment which is always a good thing.
Make sure you take a look at the Best Practice to Secure Office 365 Guide with more than 18 security tips.
The video below from Microsoft is really great to inform your users, so even the most inexperienced user is able to enable MFA.
You may also like this article about using OneDrive to safely store the user’s desktop, documents, and image folder.




Hello, I really like your blog, I have a problem with mfa, I activated it in my organization and until today everything was going well but I activated something that I shouldn’t have and now when I create a user and activate mfa it only lets them validate with the microsoft authenticator app, the sms or call options no longer appear as before, what can I do?
Check this article, you might have disabled the methods in Azure.
Hi again,
Following from my previous comment…
It seems that our organization may be in a legacy mode (because it was configured before August 2017) and something called “Modern authentication” needs to be enabled in our tenancy before clients like Outlook 2013 for Windows or later become compatible with MFA. The MS article I found is below:
https://docs.microsoft.com/en-us/microsoft-365/admin/security-and-compliance/set-up-multi-factor-authentication?view=o365-worldwide#turn-on-modern-authentication-for-your-organization
I have not yet tested this, but it might be worth adding to your guide as it seems quite comprehensive.
I appreciate your article prompted me to dig harder into the issue. Hopefully, we get it fixed now.
Thanks
Yes, you will need to enable modern authentication. I actually have written an article about it, which you can find here. But I will also mention it in this article.
Hi,
I like this article but you say that the “App Password is for applications where you can’t use the MFA” specifying GMail and external Apps. However, it seems that Microsoft Outlook (yes their own product) doesn’t support its own MFA. We also tried the App password in 365Mapper and it does not work so it seems it is only compatible with Microsoft App Password approved products from our testing. So if you want clients to continue to use their Outlook App then you do need to set your users to “Enforce” mode and generate an App Password to fix the Outlook login loop that occurs after enabling MFA.
Unless you can confirm a workaround to this?
Thanks
Rudy, just came across this article. very nicely written and simplified. However, I am not sure if I understand correctly the implications of setting up app password. once created, where will it be used and how. Can you please shed some light on it.
Thnaks,
Hi Raj,
The app password is used for applications where you can’t use the MFA. Almost everything supports MFA these days, but sometimes with PowerShell for example, you will need to use an app password.
Care to share some of this? Or is it in another blog? I have to follow you! lots of great info!
Stay safe!
Hey Mike,
Thanks. But what do you want me to share or what information are you looking for?
So sorry! i think I was referring to the line: . So make sure you have informed your user up front with a clear user guide on the steps they have to take.
Ah, well I only have a user guide in Dutch. I have created a SharePoint news page where I write this kind of user guide for my users. So I can’t really share it.
Thank you but some questions:
1) You turn on MFA per user. When you set up a new user, you have to remember to turn it on for them also?
what do you think about / is there a way to turn on MFA for the tenant then turn it off for everyone except a few as you roll it out? That way, new users get MFA from the start?
2) Microsoft changes the admin panel (often), right? Since your article, the manage MFA button is not there / have to go into a user, right? (step 2) and I don’t see those settings – changing the 14 days to more is important for us.
3) as you point out – if a user gets texts or has to supply a 6 digit number on the authenticator app.. if they want to change to the allow / deny notification, can you tell me where that is?
Hi Mike,
1. Yes, I still turn it on per user. If you have Azure p1 plan for your users, you can create conditional access policies allowing you to automatically enable MFA for your users. If you don’t have a p1 plan, you can only enable Security Defaults in Azure, but that has a couple of downsides. It’s enabled for all user accounts (and in my experience, you always have some system accounts where MFA won’t work). And the users can only use the Authenticator App.
2. I have the latest Admin panel and the button are still there. Make sure you enable the “new admin center” in the top right corner.
3. Users can change that themself. In Office 365, they can click on there user icon in the top right corner > view account > Security and Privacy > Additional security settings (4th option) and then the first option.
Our multi factor authentication is set up through our on Prem AD. Somewhere in the process of syncing the mobile numbers and personal email addresses are showing up in O365. Is there a setting somewhere to stop those from syncing?
We use multi-factor authentication with O365 but do not want everyone in the organization to see every users mobile number and/or personal email address. How can we continue using multi-factor authentication but hide that personal information from showing up in exchange, sharepoint, etc?
There personal mobile phone won’t be listed in the global address in Exchange. The users can install the app on their mobile (or use SMS if they want) and enter a mobile number them self. I just double-checked it with a user from which I know doesn’t have a business phone (so she is using there own) and here number isn’t listed in Office365.
Our mfa is through our on prem AD. Is there a setting in O365 to stop mobile / personal emails from syncing up?
I am not really sure but check this article: https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfaserver-deploy#how-the-azure-multi-factor-authentication-server-handles-user-data.
Seems that email is optional, but mobile number not..
I really wish MS would allow us to use other apps for OTP’s. I hate having to force people to setup another authentication app if they already use a password manager that does it (like 1Password).
Well, that’s not only on Microsoft. I got 3 or 4 OTP’s apps, unfortunately. But I have to say, the push notification from the MSFT app is really nice.
It is possible to use other apps. The trick is that the QR code presented initially by Microsoft is for “Push to mobile”, which is AFAIK only supporterd by the Microsoft authernticator. But next to the QR code is a link to “Configure app without notifications”, clicking on this will change the QR code to one consumable by Lastpass Authenticator or Google Authenticator, and presumably most others. You can even configure multiple Apps, and change how you authenticate.