#sponsored
These days, QR code phishing is one of the fastest-growing email-based attack vectors. Attackers use the QR codes to disguise the malicious links, making it challenging for users to recognize phishing attempts.
Another problem with QR code phishing is that the attack surface moves from the secured computer endpoint to the smartphone, where the protection is often minimal and security can be lacking.
In this article, we’ll take a look at how QR code phishing works and what we can do to protect against it
Understanding QR Code Phishing
QR code phishing, notoriously known as “quishing,” has become an increasing threat as the use of QR codes in business and personal transactions grows. QR codes have become an essential tool in our digital world — you probably see them everywhere, for marketing purposes, payments, authentication, and information sharing.
However, the ease of QR code generation has also made them a favored vector in phishing attacks. Cybercriminals exploit seemingly harmless QR codes to redirect users to malicious websites or trigger the download of malware on mobile devices.
The convenience of QR codes for users parallels the convenience for attackers, as the obfuscation of URLs in QR codes makes it harder to spot a scam. And with the help of AI, it has become easier for attackers to write authentic-looking emails.
What makes QR codes Appealing for Phishing
The problem with QR Codes is that they are embedded as an image in emails. This not only makes it harder for users to detect malicious links quickly, but the security system can also only analyze it after the image is rendered.
But the problem doesn’t stop there. As we all know, you scan a QR code with your mobile device. That’s where another opportunity lies for the attackers.
Your corporate computer, for instance, is often highly secured and part of a secure network, but mobile phones—and especially personal mobile devices—are not. These devices often don’t have advanced security mechanisms that can stop malicious links or downloads.
Another issue with mobile devices is the smaller screen, which can make the content harder to read and thus make it more difficult to spot malicious links or warnings.
Examples of QR Code Phishing
Attackers design phishing emails to appear trustworthy and often convey a sense of urgency, such as an expiring password or an important document that needs the recipient’s attention. When a user scans the QR code, they may be prompted to enter their credentials for verification or to download a harmful file onto their device.

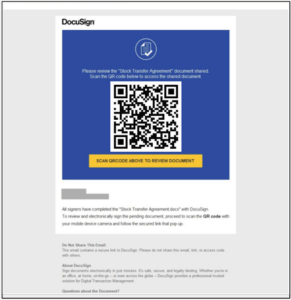
With the rise of AI, it has become a lot easier for attackers to create authentic-looking emails. AI can quickly analyze data to mimic writing styles and tailor content to specific targets, making phishing attempts more effective.
Protecting Against QR Code Phishing
Protecting against quishing brings its own unique challenges. But just like with any other security measurement, it’s all about adding layers. The first step is to try to detect and intercept the phishing mail in the mail flow.
In case we’re unable to block the mail from reaching a user’s mailbox, we can try to intercept the malicious URL. This can be done with mechanisms like safe link. Because the attack moves from the computer endpoint to the mobile device when the user scans the QR code, we also need to look into protecting mobile devices.
Microsoft 365 Defender for Office 365
Microsoft 365 Exchange Online Protection and Microsoft Defender for Office 365 are used to protect our incoming emails.
Defender for Office 365 and Exchange Online Protection uses advanced image extraction technologies to detect QR codes within emails during mail flow. The system extracts URL metadata from these codes and integrates this data into existing threat protection and filtering mechanisms.
This allows the underlying URLs to be analyzed, potentially sent to a sandbox environment for detonation, and proactively identified and blocked before reaching users’ mailboxes.
Additionally, these services use a combination of mail flow signals—including sender intelligence, message headers, recipient details, and content filtering, processed through machine learning algorithms to produce the most accurate threat verdicts.
URLs extracted from QR codes undergo further scrutiny through machine learning models and reputation checks against both internal and external sources. If you have Microsoft Defender for Office 365 Plan 1 and Plan 2 licenses, then these URLs are also sandboxed for further investigation.
Hornetsecurity Advanced Threat Protection
While not native to Microsoft 365, Hornetsecurity’s Advanced Threat Protection is a valuable additional layer to guard against quishing. This service complements Defender for Office 365 by further examining email content, including QR codes, for any signs of phishing or other email threats. It provides an external line of defense, reinforcing Microsoft’s internal security measures.
Microsoft Defender for Endpoint on Android and iOS
Because this attack vector’s process involves moving from the secured computer endpoint to the mobile device, it’s important to add adequate security measures on the mobile device as well.
An option for this would be to use Microsoft Defender for Endpoint on Android or iOS. This comes with anti-phishing capabilities and protects against malware downloads.
Implementing Multi-Layered Security Measures
To effectively protect against quishing in Microsoft 365, it’s essential to implement a robust, multi-layered security approach. This includes user awareness training, leveraging stronger authentication methods, and utilizing advanced monitoring tools.
User Awareness Training
Your first line of defense is education. User awareness training is critical in recognizing and reacting to QR code phishing attempts. Users should be aware of common phishing tactics and understand the importance of verifying the authenticity of QR codes before scanning them.
- Spotting phishing emails
- The dangers of QR code phishing
- Normal ways to reset passwords
- Detect unusual requests
Use simulations of phishing attacks to enhance this training, including those with malicious QR codes, to prepare your users for real-world scenarios.
Using Passkeys for Authentication
MFA with number matching and location is the minimum security measure that you need to implement in today’s landscape. To enhance your security even further, you should really look into the use of passkeys.
This form of Multi-Factor Authentication (MFA) significantly reduces the risk of phishing because there is no exchange of password or codes. Also, to perform the authentication, the passkey device will need to be near the device requesting the authentication.
This makes passkeys highly resistant to phishing because they cannot be reused, replayed, or phished.
Monitoring and Analysis Tools
Continuous monitoring through advanced tools like Microsoft Defender for Office 365 is crucial. It will give you an idea about how many QR code phishing attempts are carried out on your users, and which users or mailboxes are targeted the most. Make sure that those users get additional awareness training.
Wrapping up
When it comes to preventing phishing in general, it’s important to use common sense. Users need to be suspicious when they are contacted unexpectedly and are asked to perform a certain action.
If you want to know more on how you can spot phishing emails and the role of AI, make sure that you read this eBook from Hornet Security.
It’s important that they keep in mind who initiates the contact. For instance, if you’re intending to log into a site or want to share a link, QR codes can be quite convenient. However, if a QR code comes your way without warning, prompting you to do something, then you should think twice before scanning.




