Modern Authentication in Office 365 is a combination of authentication and authorization methods. It’s more secure than the Basic Authentication method, which relied only on a username and password.
As we all know by now, usernames and passwords get easily stolen. Phishing emails for example are an effective way for criminals to get the users’ credentials. This makes your tenant really vulnerable to attacks. Especially in combination with legacy protocols, like SMTP and IMAP.
Modern Authentication is enabled by default in Office 365 for tenants created after Aug 2017. But still, a lot of existing tenants are using basic authentication and/or the old protocols. Starting in June 2021, Microsoft will start with disabling the Basic Authentication method for the tenants who don’t use it.
So now is a really good time to take a closer look at Modern Authentication and how you can enable it in your Office 365 tenant.
Basic Authentication vs Modern Authentication
Basic Authentication is the old way of logging in with only a username and password. With basic authentication, each app or add-in that needs to authenticate against Office 365 will pass the credentials of the user with each request.
This means that the app has stored the credentials of the user somewhere in the application’s storage, making it vulnerable to attackers. Another problem with basic authentication is that you can’t define the permission scope for the application. So each app can have access to all the data of the user.
Modern Authentication
Modern Authentication on the other hand is based on ADAL (Active Directory Authentication Library) and OAuth 2.0. An application doesn’t store the credentials of the users, but authentication is done with tokens.
After a user logs in with their account, a token is given back to the application. The token has a limited lifetime after which it will become invalid. Another advantage of the token is that we can define a permission scope. So we can give app-only access to the mailbox of the user, but not the OneDrive for example.
Another really important advantage of modern authentication in Office 365 is that we can use Multi-Factor Authentication, also known as MFA. With MFA the user needs to log in with something he knows (username and password) and something he has, a one-time token on the mobile phone.
Enable Modern Authentication Office 365
There are a couple of steps when it comes to enabling modern authentication in Office 365. The first step is to enable Modern Authentication, but after we have enabled it we will need to phase out the basic authentication methods.
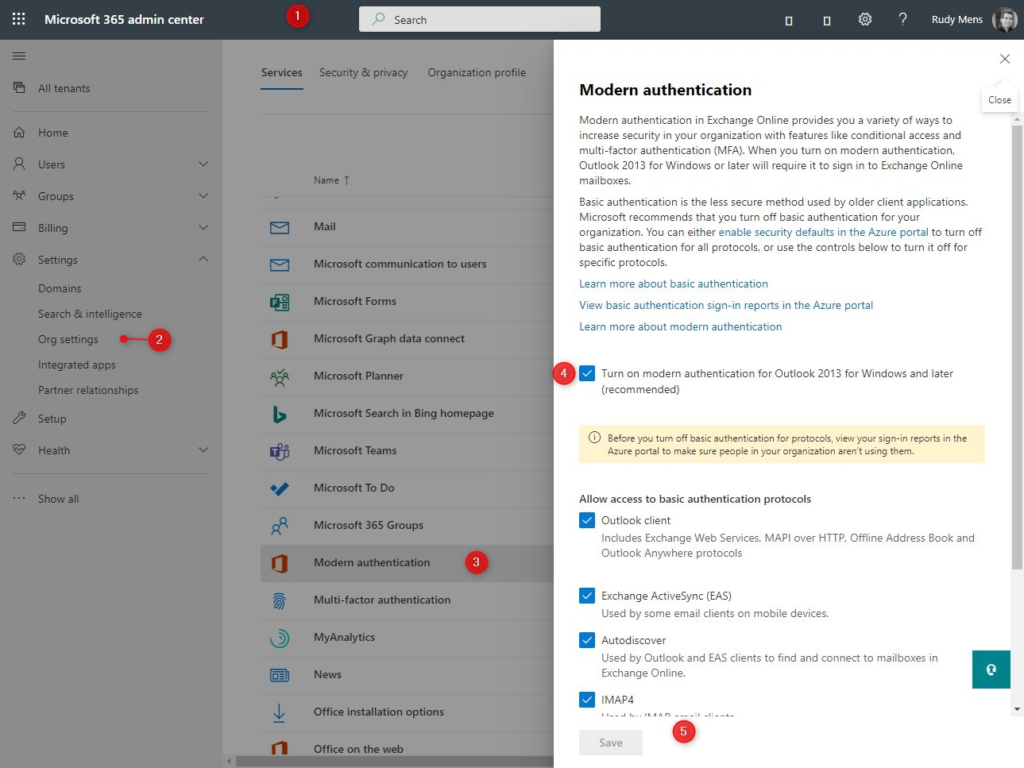
- Open the Microsoft 365 Admin Center
- Expand Settings and click on Org Settings
- Select Modern authentication
- Turn on modern authentication for Outlook 2013 for Windows and later
- Click on Save
Disabling the Basic Authentication Protocols
The next step in the process is to disable the basic authentication protocols. Now you can’t just turn them all off, because most users and probably also some business applications are using them. So the first step is to find out which users and applications that are.
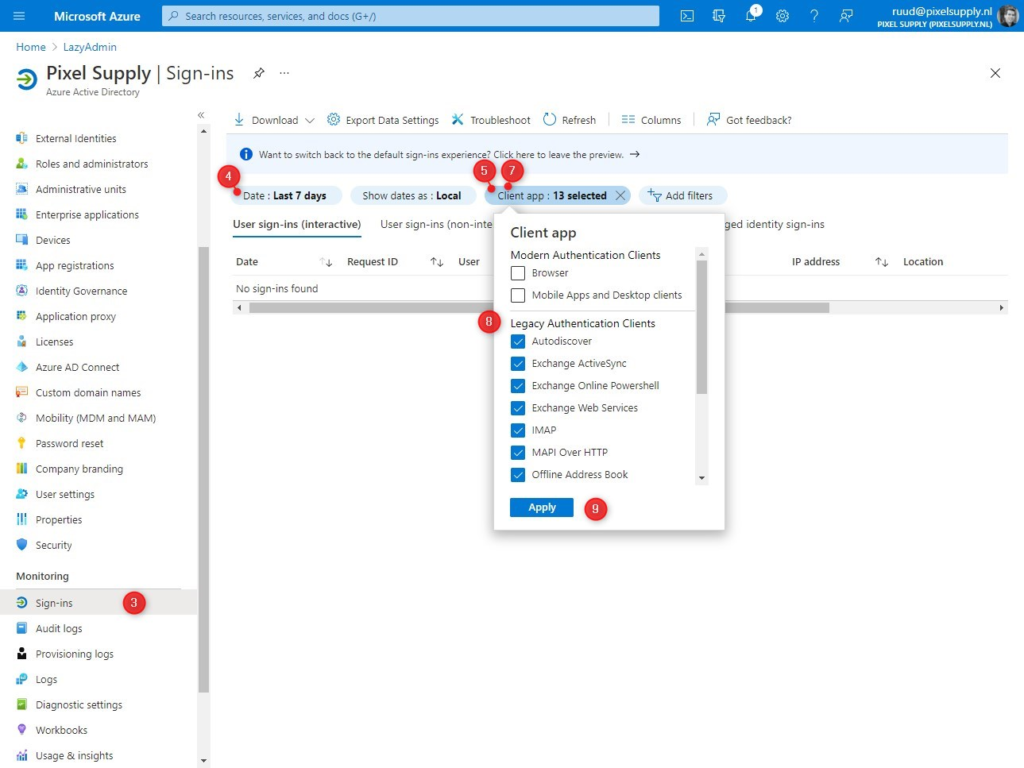
- Login to portal.azure.com
- Open the Azure Active Directory
- Click on Sign-Ins
- Change the date range to the last 7 days
- Click on Add filters
- Choose Client App
- Click again on the filter (now labeled client app)
- Thick all Legacy Authentication Clients
- Click on Apply
This will list all sign-in events from the last 7 days with the user and application that is used. You can use the list to migrate the applications to the modern authentication protocol. Most sign-in events will probably from native email clients on mobile phones.
The easiest option is to switch to the Outlook App on Android and Apple devices. It’s possible to use Apple Mail, but your users will have to remove the account first and then re-add it again to switch over to modern authentication.
You can read more about turning off the basic authentication protocols in this article, where I also have included a couple of PowerShell scripts.
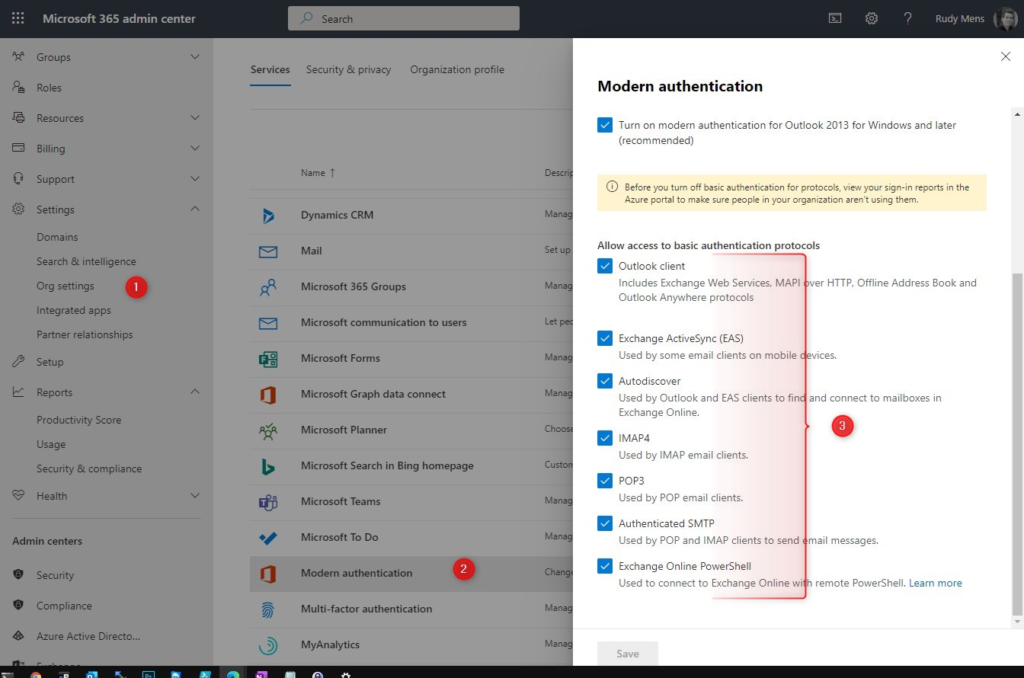
If you have migrated all applications then you can turn off the basic authentication protocols. You can do this in the Microsoft 365 Admin Center:
- Expand Settings and click on Org Settings
- Click on Modern Authentication
- Turn off all basic authentication protocols.
- Click Save.
Outlook Modern Authentication
To use Modern Authentication with older versions of Outlook you may need to change some settings on the client-side. New versions of Outlook, 2019 and Outlook for Microsoft 365 do support it out of the box.
What you need to configure depends on the Outlook version that you are using:
| Modern Auth Supported | EnableADAL reg key required | Force Modern Auth required | MAPI/HTTP required | |
|---|---|---|---|---|
| Outlook 2010 | No | – | – | – |
| Outlook 2013 | Yes | Yes | Yes | Yes |
| Outlook 2016 | Yes | No | Yes | Yes |
Outlook 2010 doesn’t not support Modern Authentication. Your only option is to upgrade Outlook.
Outlook 2013 Modern Authentication
If your organization is using Outlook 2013, then you will have to enable Modern Authentication manually. Outlook 2013 will keep using the basic authentication method by default. But we can force it to use Modern Authentication by setting a couple of registry keys on the clients.
# Change EnableADAL to 1 HKCU\SOFTWARE\Microsoft\Office\15.0\Common\Identity\EnableADAL # Change Version to 1 HKCU\SOFTWARE\Microsoft\Office\15.0\Common\Identity\Version
Outlook will now try to use modern authentication first, but if you want to force, so it won’t fallback to basic authentication then you will have change the following key to 1 as well:
HKEY_CURRENT_USER\Software\Microsoft\Exchange\AlwaysUseMSOAuthForAutoDiscover
If the keys don’t exists then you can simply create them. They are all DWORD values.
Outlook 2016 Modern Authentication
Modern Authentication is enable by default in Outlook 2016. But Microsoft recommends to force Outlook to use Modern Authentication.
We can do this by setting the following registery key to 1:
HKEY_CURRENT_USER\Software\Microsoft\Exchange\AlwaysUseMSOAuthForAutoDiscover
Skype for Business Modern Authentication
If you are still using Skype for Business then you will need to enable Modern Authencation for Skype as well. Just like with Outlook we can set a couple of registry keys to enable it:
# Change AllowAdalForNonLyncIndependentOfLync to 1 HKEY_CURRENT_USER\Software\Policies\Microsoft\Office\15.0\Lync\ AllowAdalForNonLyncIndependentOfLync HKEY_CURRENT_USER\Software\Policies\Microsoft\Office\16.0\Lync\ AllowAdalForNonLyncIndependentOfLync
Wrapping Up
Using Modern Authentication in Office 365 is really important to protect your data. Without it, attackers can easily compromise your tenant after a successful phishing attempt. Microsoft is starting with disabling legacy protocols on tenants that they don’t use.
But to protect your tenant I really recommend starting with modern authentication as soon as possible. Also, make sure you follow this best practice guide to secure your Office 365 tenant.
If you have any question, just drop a comment below.




Very informative article Rudy. It’s been a great help so far as have others you posted. One question, are POP email logins using Modern Authentication logged anywhere? How can I verify its working before Microsoft shuts off basic auth on us in January? No more extensions for us past January.
When a custom app we have uses basic auth to retrieve mail, I see those connections in the Azure Active Directory Sign-Ins as you noted in your article.
But when I change the Client App filter to use both Modern Auth clients (Browser & Mobile apps and Desktop clients), I do not see the POP logins when we test a change to use Modern Auth.
I see the Microsoft 365 apps logging in OK. I thought the POP logins might be under Graph, but no matches there. I searched by username and the sending servers IP address, the same IP that shows when I searched for Basic auth clients. But no connections are logged when we use POP with modern auth to check the mailboxes. We would like to see some verification, and it could be useful for future troubleshooting.
Any thoughts on if and where POP logging using Modern Auth is logged? Do I need to enable something for POP logging using Modern Auth to happen? I’ve googled this and experimented for days with no luck.
I would greatly appreciate any insights you have on this. Thank you so much in advance.
Not that I know.
Hi Rudi,
I have an external vendor app that requested to make changes to our Azure tenant, the reason for thier request is all Outlook 365 email communication will no longer support Basic Authentication, for sending and receiving emails through our internal 365 service from 1st October. Currently vendor web app is communicating to a specific user email address (our email address) to send emails.
My question is how do I grant the external vendor app office 365 exchange api access only to one specific user email address instead of giving the app access to our entire entire environment?
Many thanks in advance.
In Azure > App Registration, create a new app and grant only Mail.Send permission in the Microsoft Graph API. Then limit the application permissions
I’m a little confused, if Outlook 2016 requires MAPI/HTTP for Modern Auth – how does that work? when disabling legacy auth via conditional access in azure turns off the MAPI\HTTP access?
Mapi over HTTP can’t be disabled when using Outlook 2016
Hi Rudy Mens,
I’m going to blast the comman to all-user (Office13 and Office16). What happens if Office16 user is also add registry EnableADAL and Version?
Looking forward to your reply
Won’t be a problem.
Great article. I have a question finding it hard to get an answer.
We have a simple environment with 16 users. A small number of these users are shared user accounts. Due to the size of the organisation we cannot afford to create user accounts for all possible users because some of these are on rotation/internships and the like. I have secured what they have access to, so this works reasonably well.
We are having a LOT of issues with 365 Group Calendars not syncing properly and the answer seems to be that we need to enable Modern Authentication. I had originally disabled this because MFA is difficult to manage for the shared users. If I enable Modern Authentication, can I easily turn off MFA for the shared users? Do I require Conditional Access rules here?
If Conditional Access rules are the solution, we will need to move from MS 365 Business Standard to Business Premium, which includes Azure Active Directory Premium P1. This will incur some additional expense for us.
Are you able to point us in the right direction? Thanks!
Conditional Access would be the best solution. This even allows you to only require MFA when the users are outside your company network.
But, you can also enable MFA per user: In the Admin center, go to > Active Users > Click on the 3 dots (more options, in the Add a user menu bar) and select Multi-factor Authentication. You can now select individual users and enable MFA for them.
Besides that, I would recommend disabling all the legacy protocols that you don’t need and check this Best Practice Security Guide for Office 365
Thanks Rudy! I will need to go down the Conditional Access path, better for future.
Hi Rudy,
Many thanks for this. From your experience – simply enabling Modern auth and initially not disabling the older protocols – have you seen any issues?
I’ve a need to enable it but fearful of implications.
T
You can leave the old protocol enabled, but then the modern authentication won’t offer you any extra security. Attackers can then still use the old protocols and only the username/password obtained from a phishing mail to get access to your mail for example.
Hi, RUDY MENS
I am about to take actions, but before that, I have a question: are there impacts to the client after enabling this feature?
I have many 2013 version Outlook, so, you know
Looking forward to your reply
As mentioned is Outlook 2013 supported, so it should work fine.